Meet the IT Heroes

Meet the interstellar crew guiding you through the digital cosmos…
Click forward when you're ready to begin your mission.
📚✏️ Slideshow content

🧠 Network Cable Types
Let’s plug into the basics! These brave characters will guide you through the colorful world of STP, UTP, Coaxial, and Fibre Optic cables—what they’re made of, how they connect, and where they’re used. From CAT6 to optical light, you're about to learn what really keeps the digital galaxy connected. 🌐⚡
Cable Types Diagram

Here's a visual breakdown of each cable type with their connectors and properties. From RJ45 to LC and F-type, these labels will help you recognize the tools of the network trade. Just tap on any part of the comic to zoom in and absorb!
🔌 RJ Connectors 1

These are the classic RJ45 connectors—snapping Ethernet cables into network ports for reliable data links. Perfect for gigabit speeds! ⚡🌐
📞 RJ Connectors 2

Say hello to the RJ11 connector—smaller than RJ45, used for telephone lines and DSL modems. 📠🔗
🛡️ STP vs UTP Categories 1

STP (Shielded Twisted Pair) blocks EMI with foil shielding, while UTP (Unshielded) is lighter and cheaper—choose based on your interference environment. 🌪️🚫 vs 💡💰
📈 STP vs UTP Categories 2

From Cat5e to Cat6a and beyond—higher categories mean tighter specs, faster speeds, and better crosstalk control. 🚀🔍
📊 STP vs UTP Categories 3

Categories map out performance tiers—Cat3 for legacy voice/data, Cat6/6a for gigabit+, and Cat8 for data centers. Choose your speed! 🏎️⚡
📺 Coaxial Cables

Coaxial cables carry RF signals with a central conductor and braided shield—ideal for cable TV, satellite, and broadband internet. 🛰️🔵
🔌 RG Coaxial Types

Meet RG-6, RG-59, RG-11, and friends—each “RG” number defines impedance and attenuation for different video and data applications. 📡📶
🔧 TNC & MCX Connectors

TNC (threaded) offers rugged, wideband RF connections; MCX (micro) is compact for tight spaces. Both keep your signals locked in place! 🔩📻
💡 Fibreoptic Cables

Fiber-optic cables transmit data as pulses of light—perfect for ultra-high bandwidth and long-distance links. 💡🌐
🌈 Multi-Mode Fiber (MMF)

Multi-mode fiber uses multiple light paths—great for short-reach links like data centers, with lower-cost transceivers. 🏢💾
🔌 Fiber Optic Connector Types

LC, SC, ST, FC—each connector has unique form factors and latch styles. Pick one for your network’s insertion loss and space needs. 📏🔗
🌐 Types of Networks

From LAN (Local) to WAN (Wide), MAN (Metro), and CAN (Campus)—choose the right scope for your organization! 🏠🏙️
🚌 Bus Topology (1.0)

A single backbone cable with terminators on each end—simple but prone to collisions and bottlenecks. 🛣️🚏
💍 Ring Topology (1.1)

Nodes form a closed loop—data circles around until it reaches its destination. Offers redundancy if you use dual rings. 🔄🎯
⭐ Star Topology (1.2)

All devices connect to a central hub or switch—easy to manage, but a single point of failure. ⭐🛠️
🕸️ Mesh Topology (1.3)

Every node links to every other—max redundancy and resilience, but high cabling costs. 🔀🔗
🌳 Tree Topology (1.4)

Hierarchical stars linked by a backbone—scalable and easy to expand, blending star and bus benefits. 🌲📡
🌌 IPv6 Universe

Step into the IPv6 realm! This visual kicks off our journey with a lone explorer amid neon data streams—ready to unveil why 128-bit addresses are the next frontier of our digital galaxy. 🚀✨
🪐 IPv6 Explained
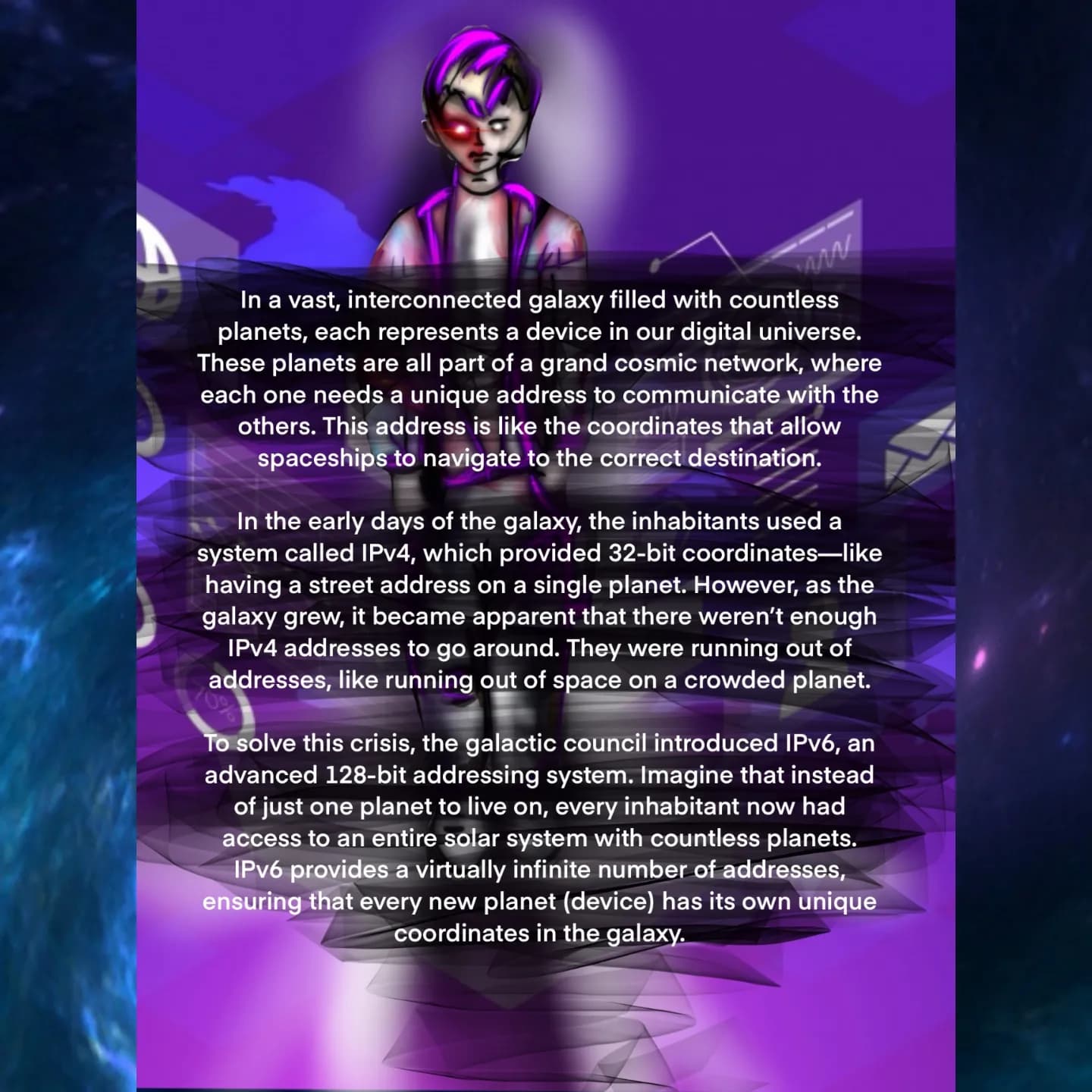
Imagine each device as a planet in a sprawling cosmos—this panel uses that galactic metaphor to show how IPv6’s vast address space keeps every “planet” uniquely reachable. 🌠🔭
🔍 Packet Sniffing
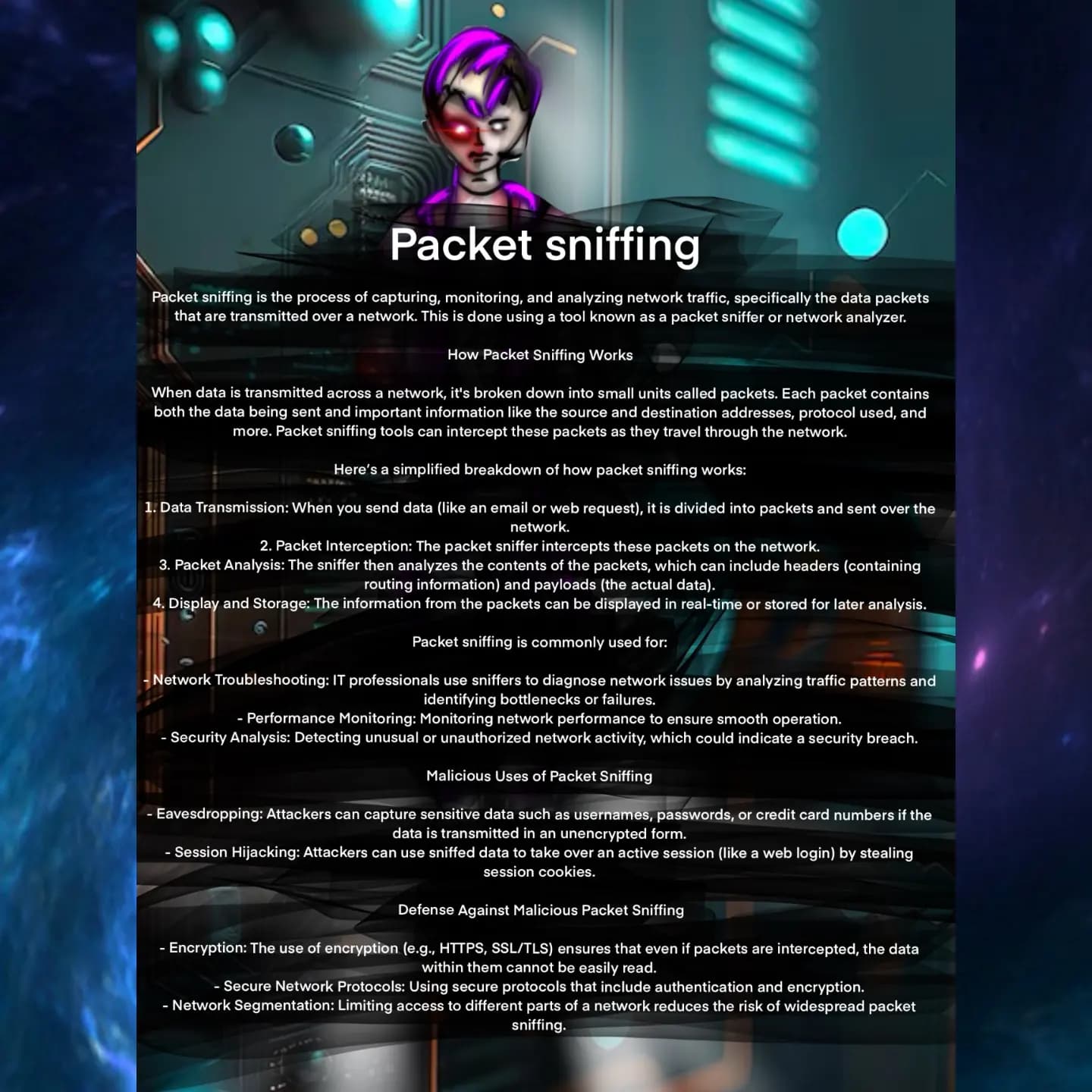
Peek behind the curtain of network traffic! This graphic breaks down how a packet sniffer captures, analyzes, and displays data packets—whether for troubleshooting or security monitoring. 🛡️📡
🛠️ Packet Spoofing
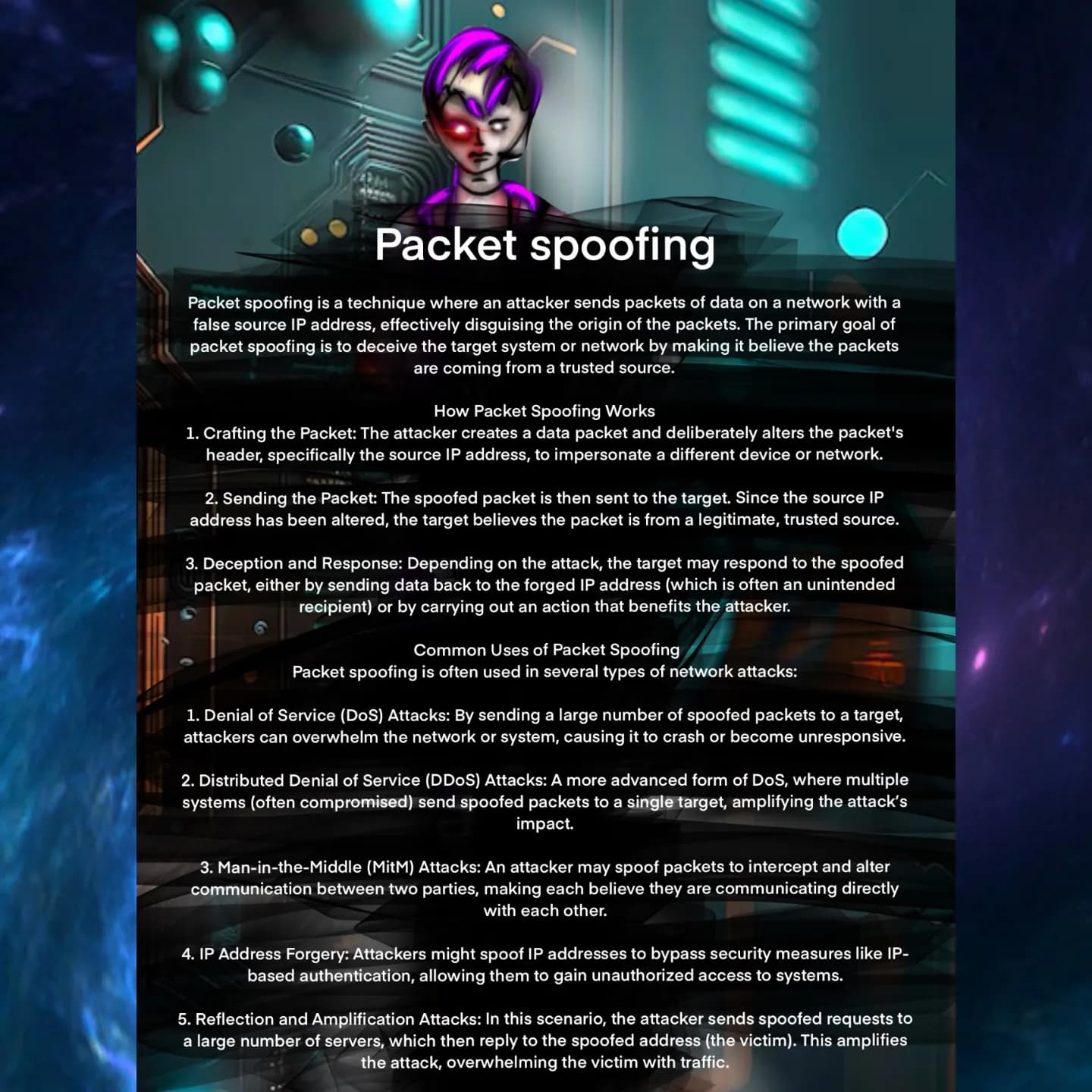
When attackers disguise packet origins, it’s called packet spoofing. This scene shows how forged headers can trick systems—leading to DoS, MitM, and more. 🎭⚠️
🔢 IP Decimal vs Hex

Ready to decode addresses? This intro frames the showdown between decimal (base-10) and hexadecimal (base-16) IP formats in a sleek, futuristic cityscape. 🌆🔮
🔟 Decimal Format

In plain-spoken terms, decimal format splits an IP into four octets (0–255). This panel walks you through “192.168.1.1” and why each chunk fits neatly into our everyday number system. 🧮✨
🔷 Hexadecimal Format

For the tech-savvy explorer, hexadecimal format converts each octet into base-16 (0–9, A–F). Learn how “192.168.1.1” becomes “C0.A8.01.01” in this high-tech tutorial. 🖥️🔢
🖥️ Network Architecture

Meet Scientist 7 and his trusty sidekicks as they unveil the five key network architectures—from simple two-tier setups to hybrid cloud designs. Ready to build your perfect digital highway? 🚧🌐
🏛️ Three-Layer Architecture

The classic core-distribution-access model keeps large networks organized and scalable. Learn how each layer handles specific roles—from end-device connectivity at the “street level” to lightning-fast backbone transport. ⚡🔗
🔀 Collapsed Core Architecture

When simplicity wins, merge your core and distribution into one collapsed core layer. Ideal for smaller campuses, this two-tier design cuts costs and management overhead—while still supporting robust access controls. 🔄🏢
🌿 Spine-Leaf Architecture

Data centers love spine-leaf for its non-blocking fabric: every leaf switch talks directly to every spine switch, eliminating bottlenecks and maximizing redundancy. Scale horizontally by adding more spines or leaves! 📈🤝
🔗 Dual-Core Architecture

For mission-critical uptime, deploy two core layers in an active-active or active-passive redundancy model. If one core fails, the other takes over—perfect for financial systems, emergency services, and 24/7 operations. 💪🔌
☁️ Cloud/Hybrid Network Architecture

Leverage on-premises hardware and cloud scalability with a hybrid network. Host critical resources locally for low latency, while offloading bursty workloads and global access to the cloud. Flexibility meets performance! 🌍🔀
❓ What Is the TCP/IP Model?
Launch into the backbone of the Internet! This vivid graphic poses the big question—how do our devices package, ship, and deliver data across the global network? Buckle up for a four-layer deep dive. 🌐🚀
🔑 Key Protocols in the TCP/IP Suite

Meet the protocol cast: IP routes your packets, TCP guarantees delivery, UDP trades reliability for speed, and HTTP/FTP/SMTP/DNS power the apps you love. Ready to see how they stack up? 📦🔄
🔗 Layers 1 & 2: Network Interface & Internet

At the ground floor, the Network Interface (Link) layer handles framing, MAC addressing, and the physical handshake (Ethernet, Wi-Fi, ARP). One floor up, the Internet layer tackles logical addressing (IP), routing, and fragmentation—guiding your bits through the maze. 🛣️📶
⚙️ Layers 3 & 4: Transport & Application

The Transport layer (TCP/UDP) ensures data streams stay in order, control flow, and recover from errors. At the top, the Application layer (HTTP, FTP, SMTP, DNS) speaks the languages your apps understand—formatting, processing, and exchanging data seamlessly. 🔄📲
🌌 Network Classes: The Galactic Channels

Journey through the five network classes—our “galactic channels”—that govern how data flows across star systems. From the vast central hubs to the mysterious forbidden zones, prepare for an interstellar address tour! 🚀✨
🛰️ Class A & Class B Networks
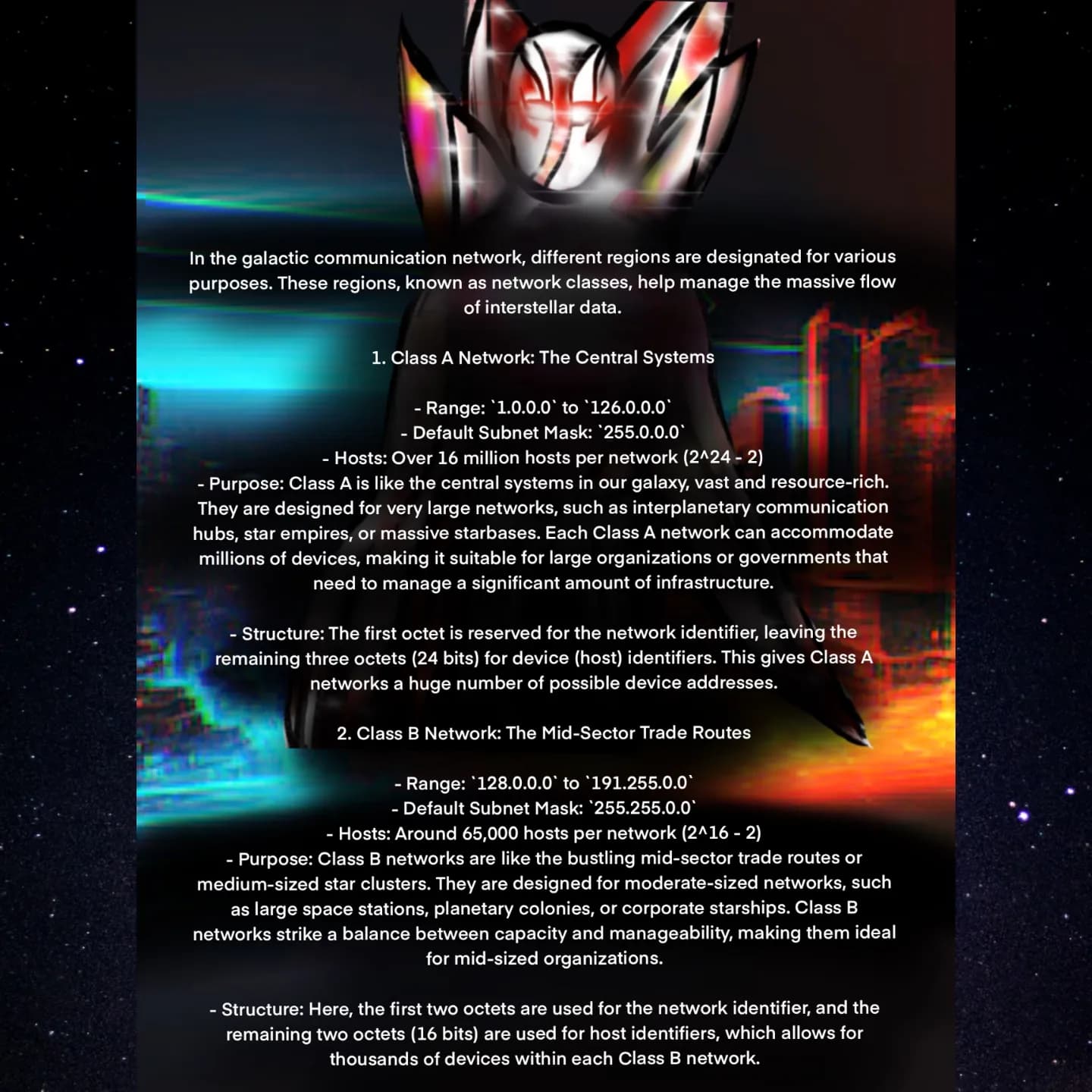
Class A: The central systems (1.0.0.0–126.0.0.0), hosting millions of devices—perfect for massive interplanetary empires. Class B: The mid-sector trade routes (128.0.0.0–191.255.0.0), ideal for medium-sized star clusters with ~65K hosts each. 🌠🔄
🏙️ Class C & Class D Networks

Class C: The outpost rings (192.0.0.0–223.255.255.0), supporting up to 254 hosts—tailored for small ships and research stations. Class D: The broadcast beacons (224.0.0.0–239.255.255.255), reserved for multicasting messages galaxy-wide. 📡🌐
🔒 Class E & Subnet Masks

Class E: The forbidden zone (240.0.0.0–255.255.255.255), reserved for experimental tech and future expansions.
Subnet masks act like force fields—255.0.0.0 for Class A, 255.255.0.0 for B, 255.255.255.0 for C—guiding every packet to its proper star system.
And that wraps our galactic network map: from sprawling central empires to the edges of experimental space. 🌠🗺️
🚪 Commonly Used Ports

Dive into the essential port numbers that power the internet. From file transfers to secure web browsing, these ports are your network’s doorways—let’s explore what each one does! 🌐🔑
📁 File Transfer & Remote Access (Ports 20–23)

20 & 21 – FTP: Port 20 carries data, 21 carries control commands—now mostly replaced by SFTP/FTPS due to encryption needs. 22 – SSH: The encrypted standard for secure logins, file transfers, and port forwarding. 23 – Telnet: Legacy remote shell, sends everything in plain text—avoid unless you love eavesdroppers! 🔒📡
✉️ Email, DNS & Web (Ports 25–110)

25 – SMTP: Mail servers talk to each other here (use 465/587 for secure submission). 53 – DNS: Translates names to IPs via UDP (queries) & TCP (zone transfers). 80 – HTTP: Unencrypted web traffic (redirects to 443 on modern sites). 110 – POP3: “Download-and-delete” email protocol—largely supplanted by IMAP. 📧🌍
🕰️ Time & Mail Access (Ports 123, 143 & 161)

123 – NTP: Keeps clocks in sync across servers, routers, and IoT—vital for security logs and auth services. 143 – IMAP: Manage email on the server with syncing across devices (preferred over POP3). 161 – SNMP: Network management magic—monitor and configure routers, switches, and more. ⏱️💬
🔒 Secure Web & Directories (Ports 389, 443, 465 & 587, 993)

443 – HTTPS: Encrypted web traffic via SSL/TLS—essential for e-commerce and banking. 389 – LDAP: Directory lookup service (e.g., Active Directory). 465 & 587 – SMTPS: Secure email submission (465 now legacy, 587 preferred). 993 – IMAPS: Secure IMAP for encrypted mail retrieval. 🌐🔐
💾 Secure Email & Databases (Ports 995, 1433, 3306, 3389)

995 – POP3S: Encrypted POP3 for secure email downloads. 1433 – MSSQL: Default SQL Server port for relational databases. 3306 – MySQL: Standard MySQL database access (LAMP staple). 3389 – RDP: Microsoft Remote Desktop—administer Windows machines remotely. 🗄️📟
🔄 Ports 8080, 8443 & 49152–65535

8080 – HTTP Alt: Secondary web server/testing port when 80 is taken. 8443 – HTTPS Alt: Secure web proxy/development port when 443 is busy. 49152–65535 – Dynamic/Private: Ephemeral client-side ports auto-assigned by the OS for outgoing connections. 🔄🌐
🌐 Unicast, Multicast & Anycast
Meet the three key delivery methods that drive modern networks! From one-to-one messaging to targeted group streams and nearest-node routing, these techniques shape how data travels across the internet. 🚀📡
➡️ Unicast (One-to-One)
Unicast sends data directly to a single destination IP—think of it like a private letter delivered door-to-door. Each session uses its own connection, ensuring exclusivity and reliability. 🔒✉️ Common uses: • Web browsing (your browser ↔️ server) • Online gaming (player ↔️ game server) 🕹️🌐
📣 Multicast (One-to-Many)
Multicast broadcasts data to a specific group of subscribers—like sending a newsletter only to your mailing list. Devices “join” or “leave” multicast groups to receive streams efficiently. 📬🌍 Key protocols: IGMP for group membership, PIM for routing. Key uses: • Live video streams & webinars 🎥🖥️ • Multiplayer game state updates 🎮🔄
🏃 Anycast (Nearest-Node)
Anycast directs traffic to the closest server among a pool sharing the same IP—like calling the nearest help desk no matter where you are. Routing protocols (e.g. BGP) pick the optimal path. 🛰️🏃♂️ Common uses: • CDN edge servers for fast content delivery 🌐⚡ • Global DNS resolvers for low-latency lookups 🗺️🔍
🦕 Preparing Data for Launch
🚀 Welcome to the magical realm of data packet transmission! These three dino-astronauts are preparing your data to blast off across the network. From application to physical layer, every detail is packed with purpose and precision. 🌐✨
🛰️ Journey Through the Network
🛰️ As our packet zooms across the network, it hops from router to router like a space shuttle bouncing through stargates. Each hop brings it closer to its destination, while routing and error-checking keep the journey on course. 🧭🔧
📦 Data Delivered & Unwrapped
🌟 Touchdown! On the receiver's side, the process reverses like decoding a secret space transmission. Headers are peeled back, layer by layer, revealing the precious data inside—mission complete! 📦✅
🕵️♂️ Meet ARP: The Address Detective
🌌De-encapsulation process initiated... 🕵️♂️🔍
🛸 NAT: The Address Translator
🛸 Say hello to NAT and ARP! When your whole fleet wants to visit the internet but only one public IP is available, NAT steps in as mission control. 🧠🌍 It rewrites addresses like a cosmic translator, helping devices share a single IP in harmony. 🔄📡
🎁 Layered Transmission: Gift-Wrapped Data
✨ Here’s how data transmission works at each layer—from your app to the wire! Every layer adds its own tag to make sure your information gets to the right place safely and quickly. Think of it like wrapping your gift with care at each step! 🎁💌
🌐 Guided by the Stars: Hop-by-Hop Routing
🧭 Hop-by-hop, the frame travels the galactic highway of routers and switches! MACs and IPs light up the path, while routers steer your message through the best cosmic route. 🌐🚥
Multi-Protocol Label Switching (MPLS)
🚀 Meet MPLS, your fast-lane intergalactic navigator! Instead of scanning every cosmic route, it tags your packets with special labels for swift and efficient travel across WAN space highways. 🛰️🌌
MPLS Label Assignment & Switching

🧩 As data zooms into the MPLS realm, it’s handed a label—like a teleport pass! Routers no longer need to think twice—they just check the label and beam it to the next hop. ⚡🛰️ It's label swapping at light speed! 💫
MPLS Path Setup & Benefits

🌠 Before the transmission even begins, MPLS crafts a path through the stars using LDP or RSVP-TE protocols. The result? 🚦 Less lag, smarter traffic lanes, prioritized packets, and a network that scales like a nebula expanding! 💡📈
Multipoint Generic Routing Encapsulation (MGRE)
🧠✨ Welcome to MGRE—a protocol wizard that connects multiple starbases through a single portal! It’s like having one magic wormhole connecting multiple galaxies at once! 🌀🌌
GRE Overview & Packet Structure

📦 GRE wraps your packet like a gift in a special space envelope—containing not just what it is, but also how it should fly through the cosmos. Protocol? Check. Route? Ready. 🚀📬
GRE and MGRE Key Features

🌈 GRE and MGRE are like digital duct tape—wrapping any protocol, no matter how funky! MGRE upgrades the spellbook, letting one tunnel talk to many, and discover new endpoints dynamically like a space scout! 🧪🔮
How MGRE Works & VPN Use Cases

🛸 With MGRE, routers create tunnels like wormholes—dynamic, flexible, and ready to link up any distant system! Perfect for VPNs or roaming outposts that come and go. MGRE adapts like a galaxy with built-in intuition. 🔄🌍
🔌 iSCSI

💾 iSCSI lets computers treat faraway storage as if it’s right next to them! It sends SCSI commands over IP networks, making it a cost-friendly and flexible solution for modern data centers and cloud setups. 🌐📦
🌐 How iSCSI Works

🚀 The initiator sends commands to the target (a storage device) through the network using TCP/IP. No fancy cables—just good ol’ Ethernet! 🧠💻 Perfect for scalable storage adventures. 🪐
🧬 Virtualized iSCSI Storage

🏢 Virtual machines treat iSCSI storage like it’s local—even when it’s not! That means flexible data access, distributed storage, and high availability from anywhere in the data cosmos. 🌟📁
🔐 The CIA Triad in Cybersecurity

🔒 Confidentiality, Integrity, Availability—your cybersecurity holy trinity! 🔐 The CIA model protects data from prying eyes, corruption, and downtime. It’s the guardian shield of your information. 🛡️💡
📊 Security Information Management (SIM)

📚 SIM gathers logs from security devices and analyzes them for patterns. Great for audits and compliance—it’s like keeping a diary of your network’s safety! 📝🧠
🛎️ Security Event Management (SEM)

🚨 SEM detects live threats in real-time and jumps into action! It monitors events as they happen and can respond like a superhero with a mission. 🦸♂️⚡
🌍 SIEM – Security Intelligence Powerhouse

🧩 SIEM combines SIM’s logging powers with SEM’s real-time detection skills to form one ultimate security force. It’s like Voltron for your network. 🧠📡
🚀 SIM, SEM & SIEM — The Security Trio

🔎 SIM logs, SEM watches, and SIEM unifies—together they defend your systems from digital danger. Each one plays a vital role in modern IT fortresses. 🏰💡
📍 Demarcation Points Explained
📍 Demarcation Points Explained — This illustration or guide breaks down key networking concepts to help you master IT fundamentals. ✨💻
📦 What is a Smartjack?

📦 What is a Smartjack? — This illustration or guide breaks down key networking concepts to help you master IT fundamentals. ✨💻
🔬 Inside a Smartjack

🔬 Inside a Smartjack: Appearance & Components — This illustration or guide breaks down key networking concepts to help you master IT fundamentals. ✨💻
🌐 How to Connect a Router – Meet the Crew

🌐 How to Connect a Router – Meet the Crew — This illustration or guide breaks down key networking concepts to help you master IT fundamentals. ✨💻
🛠️ Router Config: Enable HTTP & Login

🛠️ Router Config: Enable HTTP & Login — This illustration or guide breaks down key networking concepts to help you master IT fundamentals. ✨💻
🔌 Physical Connections: Modem, Router & PC

🔌 Physical Connections: Modem, Router & PC — This illustration or guide breaks down key networking concepts to help you master IT fundamentals. ✨💻
⚙️ Configuration Steps for Router & PC

⚙️ Configuration Steps for Router & PC — This illustration or guide breaks down key networking concepts to help you master IT fundamentals. ✨💻
⚡ Transistors – Heroes of Electronics

⚡ Transistors – Heroes of Electronics — A visual and narrative guide into how transistors power everything from logic gates to routers. 🧠⚙️
🔄 NPN Transistor: Layers & Operation

🔄 NPN Transistor: Layers & Operation — A visual and narrative guide into how transistors power everything from logic gates to routers. 🧠⚙️
🌀 PNP Transistor: Layers & Operation

🌀 PNP Transistor: Layers & Operation 🧠⚙️
🎯 Field-Effect Transistors (FETs) Overview

🎯 Field-Effect Transistors (FETs) Overview 🧠⚙️
💡 Transistors: Functions & Applications

💡 Transistors: Functions & Applications 🧠⚙️
🔧 Supporting Tech & Transistor Synergy

🔧 Supporting Tech & Transistor Synergy 🧠⚙️
🚨 FPGA Security – Reprogramming & Complexity

🚨 FPGA Security – Reprogramming & Complexity 🧠⚙️
🛡️ Mitigation Strategies for FPGA Risks

🛡️ Mitigation Strategies for FPGA Risks 🧠⚙️
🌐 SD-WAN vs UDN – Meet the Crew

🌐 SD-WAN vs UDN — This scene dives deep into network evolution and virtual cosmos creation 🌐✨
🧠 SD-WAN: Centralized Smarts for Modern Networks
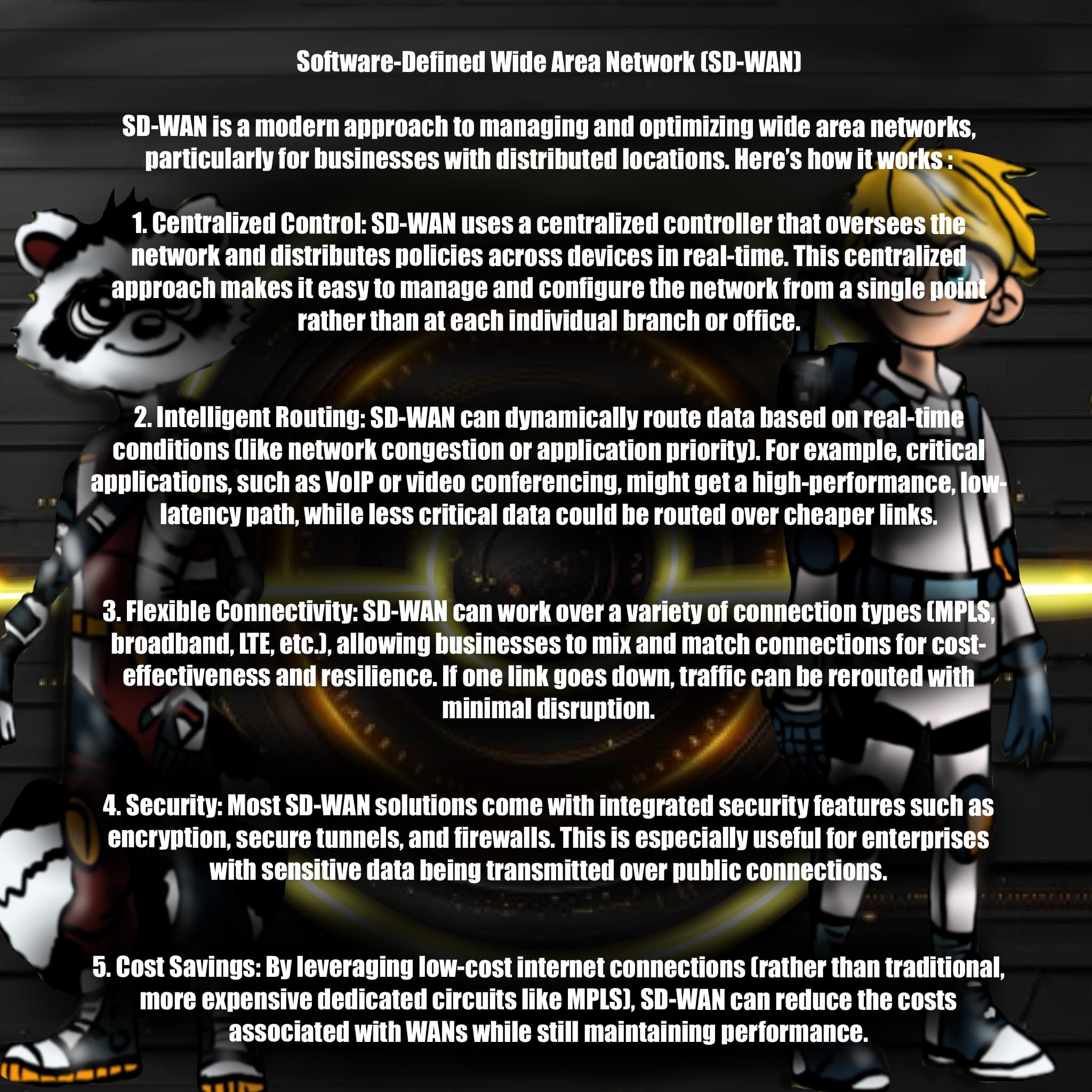
🧠 SD-WAN: Centralized Smarts for Modern Networks 🌐✨
🔧 UDN: Custom Networking, User-Controlled

🔧 UDN: Custom Networking, User-Controlled 🌐✨
⚖️ Comparing SD-WAN and UDN – Which Fits Best?

⚖️ Comparing SD-WAN and UDN – Which Fits Best? 🌐✨
🚀 Initiating Hyper-V VM – A Sci-Fi Walkthrough

🚀 Initiating Hyper-V VM – A Sci-Fi Walkthrough 🌐✨
🛠️ Prepping the System for Hyper-V Setup

🛠️ Prepping the System for Hyper-V Setup 🌐✨
🧭 Navigating and Activating Hyper-V

🧭 Navigating and Activating Hyper-V Control 🌐✨
📦 Building Your Virtual Machine

📦 Building Your Virtual Machine 🌐✨
💾 Configuring Virtual Storage and OS

💾 Configuring Virtual Storage and OS 🌐✨
🌌 Powering and Managing Your VM Universe

🌌 Powering and Managing Your VM Universe 🌐✨
🛡️ Router Security and Hardening – Team Ready

🛡️ Router Security and Hardening – Team Ready — Follow this mission briefing to properly harden your home router and improve network security like a true space captain. 🌌🔒
⚙️ Step-by-Step Router Configuration Instructions

⚙️ Step-by-Step Router Configuration Instructions — Follow this mission briefing to properly harden your home router and improve network security like a true space captain. 🌌🔒
🔐 Setting WPA3 and Enabling SSID Broadcast
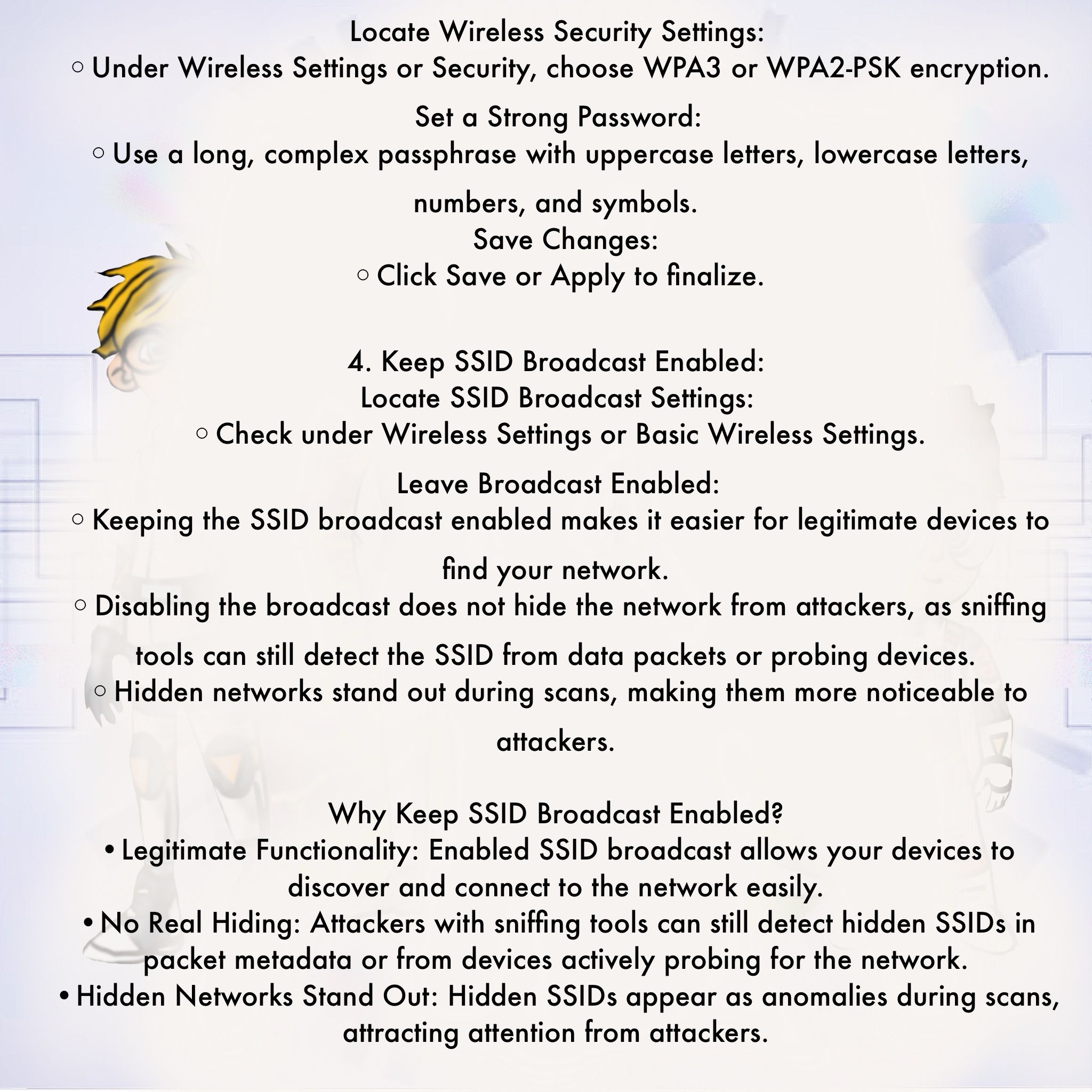
🔐 Setting WPA3 and Enabling SSID Broadcast 🌌🔒
📡 SSID, WPS, and Guest Network – Security Insights

📡 SSID, WPS, and Guest Network – Security Insights 🌌🔒
🔧 Disable WPS & Update Firmware for Protection

🔧 Disable WPS & Update Firmware for Protection 🌌🔒
🧠 Hypervisors vs Containers – The Showdown Begins

🧠 Hypervisors vs Containers – The Showdown Begins — Explore how hypervisors and containers compare in architecture, efficiency, and use cases. A must-know battle in the world of virtualization! 🚀💾
🖥️ Hypervisors – Virtual Machine Masters
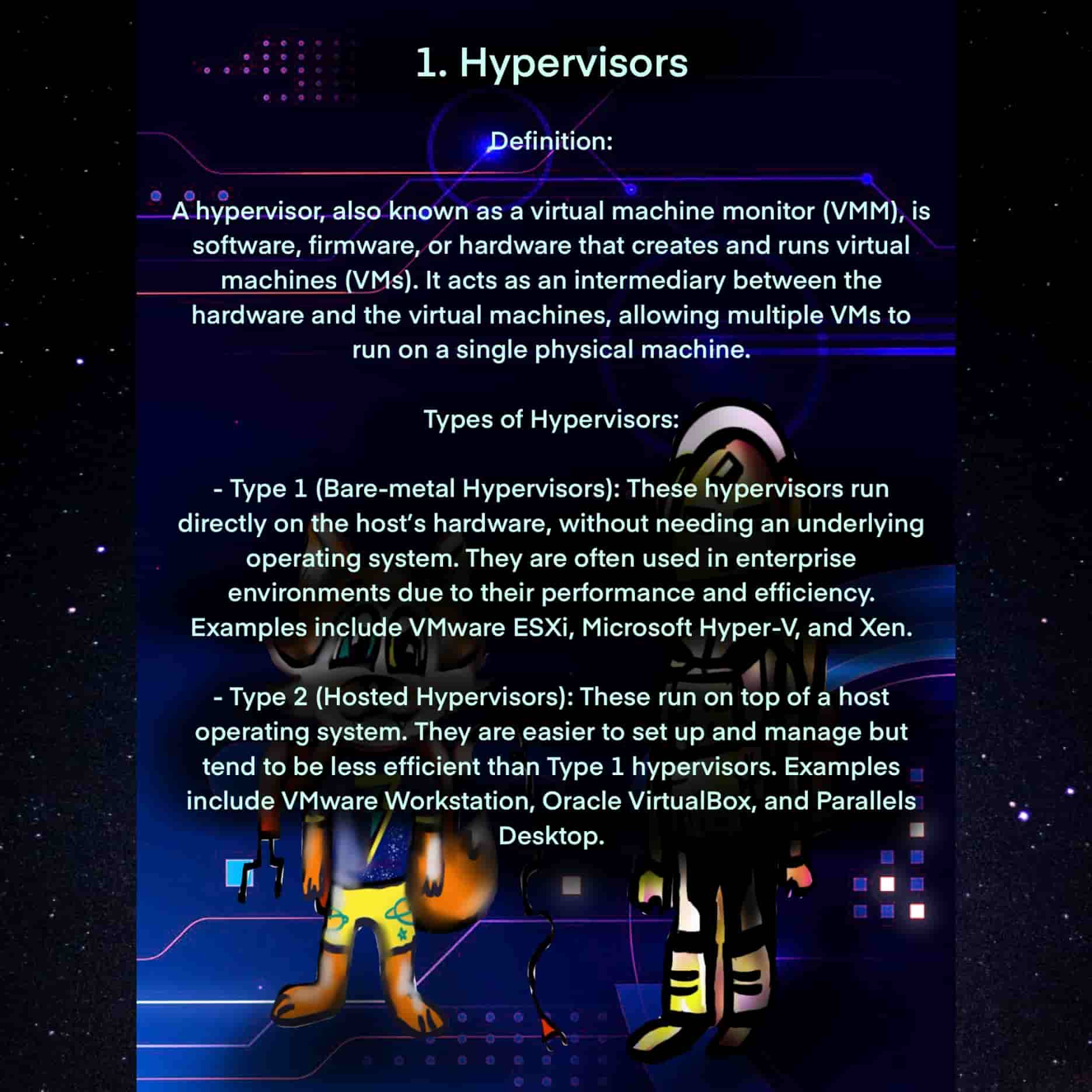
🖥️ Hypervisors – Virtual Machine Masters
⚙️ How Hypervisors Work

⚙️ How Hypervisors Work — A must-know battle in the world of virtualization! 🚀💾
📦 Virtual Containers – Lightweight & Scalable

📦 Virtual Containers – Lightweight & Scalable — Explore how hypervisors and containers compare in architecture, efficiency, and use cases. A must-know battle in the world of virtualization! 🚀💾
🔬 How Containers Work

🔬 How Containers Work 🚀💾
⚔️ Key Differences: Hypervisors vs Containers

⚔️ Key Differences: Hypervisors vs Containers 🚀💾
🔐 Network Defense Layers – Guard Your Domain

🛡️ Explore the multiple layers of network security and learn how a single misconfiguration can leave your domain vulnerable. ⚠️🔧
🛡️ First Line of Defense – Perimeter Security

🚪 Routers and firewalls form the walls and gates of your network fortress—configure them correctly to keep attackers at bay! 🏰🔒
🔍 Second Line of Defense – Threat Detection & Prevention

👀 IDS, IPS, and proxy servers monitor and block malicious activity—don’t let misconfigured alerts leave you blind to threats! 🛑🔐
🔑 Third Line of Defense – Endpoint Security & Access Control

💻 NAC, antivirus, and EDR keep your devices locked down—verify every user and endpoint before granting access. 🖥️👤
🔒 Fourth Line of Defense – Data & Identity Protection

🗝️ Encryption, MFA, and robust backup solutions safeguard your critical data and identities—protect the keys to your kingdom! 📂🔐
📚 ITIL 4 Intro

🔍 Explore the foundations of the Information Technology Infrastructure Library (ITIL) — the go-to best practice framework. 🌐⚙️
🤖🦊🛠️ ITIL Team – Meet the Guardians of ITSM

✨ Get introduced to our ITIL heroes who will guide you through the service management journey. 👩💻🚀
🔍 What Is ITIL?

🏛️ Learn how ITIL was born from the UK government and has evolved into a modern framework (ITIL 4) that integrates Agile, DevOps. 📜🔄
🔄 ITIL Service Lifecycle – Five Key Phases

🚀 Dive into the heart of ITIL: Service Strategy, Service Design, Service Transition, Service Operation. 🏗️📈
📈 Continual Service Improvement

🔄 Learn how CSI drives ongoing enhancements.
🛡️ Cyber Threats

Learn about the most common cyber threats
⚠️ Common Threats

Some of the common terminology for cyber threats.
🔐 Data Protection: Hashing, Salting & Encryption

Learn more about hashing, salting and data encryption.
🛠️ Protection Methods & Best Practices

Learn about the best practices to keep your data safe.
🧬 Programming Languages Overview

💻 Explore how we speak to computers using code! From web development to systems programming, dive into a colorful guide to coding languages. 🌐✨
🌐 Web Development Languages

🌟 HTML for structure, CSS for style, and JavaScript for logic! These tools are the backbone of websites and web apps. 🛠️🎨
🐍 General Purpose & ⚙️ Systems Languages

🐍 Python for flexibility, ☕ Java and C# for apps, and ⚙️ C/C++/Rust for system-level magic. Get to know the powerhouse languages behind your software. 🧠🚀
📜 Scripting & 🧠 Data Science Languages

🧪 Automate with Bash & PowerShell, analyze data with R, Python, and Julia! These languages shine in research, admin work, and AI. 🔍📈
🗂️ File Systems & Permissions
🔖 What is a File System?
A file system organizes, stores, and retrieves files on a storage device. It acts like a digital library catalog 📚, keeping everything in order so you can find it later. 🧠💾
🧠 How File Systems Work

✨ Breaks storage into blocks
✨ Keeps track of file names, sizes, timestamps, and locations
✨ Manages access, integrity, free space, and deleted files
📦 File System Types

⚠️ FAT32 – Simple and compatible but 4GB file limit
🌍 exFAT – Great for large USBs, cross-platform
🪟 NTFS – Windows: permissions, encryption, compression
🛡️ Securing Your File System
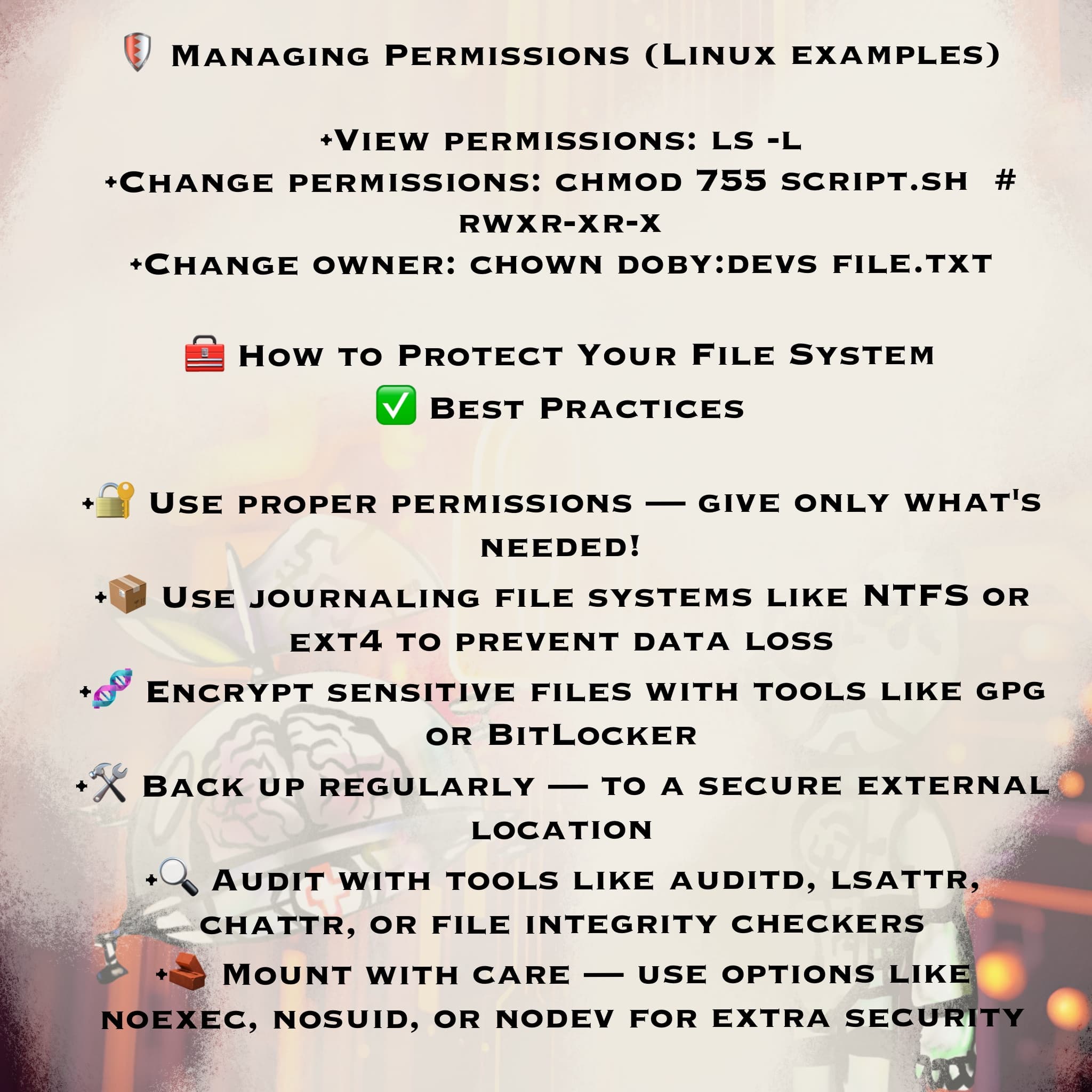
✅ Best Practices:
🔐 Use minimal necessary permissions
📦 Use journaling FS like NTFS/ext4
🍬 Encrypt with GPG, BitLocker
🔄 Backup regularly
☁️ What Is the Cloud?
☁️ Cloud computing lets you store and access data and apps over the internet instead of on your local device. It's like Netflix for your files! 🌍💻
🧠 How Cloud Computing Works

🧠 The cloud runs on data centers full of servers that store files, run applications, and deliver services remotely. It’s fast, scalable, and available on-demand! 📦🌐
🛠️ Cloud Types & Services

🛠️ IaaS, PaaS, and SaaS are the building blocks of cloud services! Plus, there are public, private, and hybrid clouds depending on how you deploy. 🚀
🔐 Cloud Security & The Future

🔐 Cloud security combines provider protections and user best practices. The future is green, smart, and decentralized with AI, edge computing, and more! 🌱🤖
⚙️ Drivers, Updates & Power – The Silent Trio Behind Your Tech

🔧 Discover how drivers, updates, and power settings silently keep your devices running smoothly — the unsung heroes of your tech setup!
🧠 What Are Drivers?
🧠 Drivers are like translators between your operating system and your hardware. Without them, your computer wouldn’t know how to talk to your printer, speakers, or graphics card!
🔋 What About Power Settings?

🔋 Power settings decide how much energy your system uses and when it sleeps or shuts off. Perfect for laptops, servers, and desktops to save energy or boost performance!
🛠️ Troubleshooting Tips
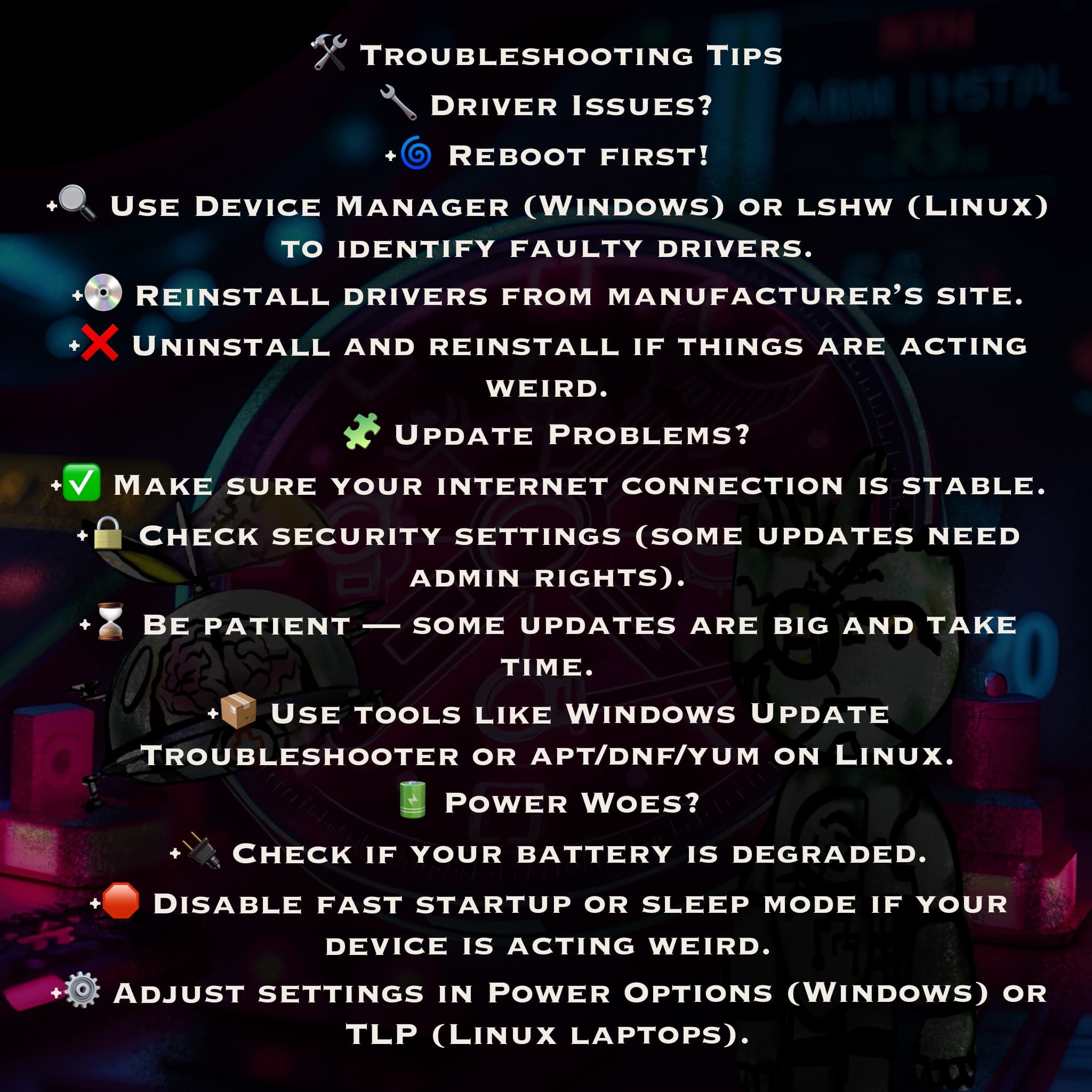
🛠️ Got weird glitches or update issues? These handy tips help you fix drivers, run updates safely, and fine-tune your power settings like a pro!
💠 Binary, Databases & SQL – The Language of Machines and Memory

💾 Meet your new IT hero who bridges the machine's brain and our digital world! Learn how binary, databases, and SQL form the core of every digital system.
🧱 What is Binary?

🧠 Binary is the foundation of everything in computing — from files to processing power. Discover how computers speak in 1s and 0s, and why those tiny bits matter!
📊 What are Databases & SQL?

🗄️ Databases keep everything organized — and SQL is the magic language we use to interact with them. Learn how to retrieve, update, and protect data like a pro!
🧠 Operating Systems – The Bridge Between You and the Machine

🖥️ Operating systems are the digital bridge that lets you speak to your device. From desktops to smartphones, they’re the reason your apps work and your files open.
🌍 What is an Operating System?

💡 An OS is the master controller of your computer—managing apps, memory, files, and more. Without it, even the most powerful machine would sit blank and confused.
🛡️ How to Secure an Operating System

🔐 Keep your system safe with updates, encryption, strong passwords, and careful user privileges. Your OS is the foundation—protect it like a digital fortress!
⚙️ Boot Process, Troubleshooting & System Monitoring – Keeping Systems Alive

🚀 Your system’s life begins with the boot process, and its health depends on how well you troubleshoot and monitor it. These three skills form the core of every IT hero's toolkit!
🥾 Understanding the Boot Process

💡 Learn how your computer starts each day—from power-on to login screen. This step-by-step journey is essential for diagnosing hardware or startup issues.
🛠️ Troubleshooting & Diagnostics for First-Line IT

🔍 Discover how first-line IT support handles technical problems—from gathering details, applying fixes, and checking logs to keeping users calm and systems running strong.
